Network Information Security Services
Industrial host security protection system
| The industrial host security protection system is positioned to provide full lifecycle security management for industrial control terminals. By installing an industrial host security guard system based on whitelist technology on industrial control terminals, it can prevent the operation of malicious programs, ensure the security and trustworthiness of terminal network links, block the spread of virus Trojans, standardize the use of external input devices, detect terminal security and ratings, ensure that terminal behavior is always within the controlled trust range, and achieve comprehensive security protection for industrial control hosts. Ensure the availability, reliability, and credibility of workstations and servers. | |
|
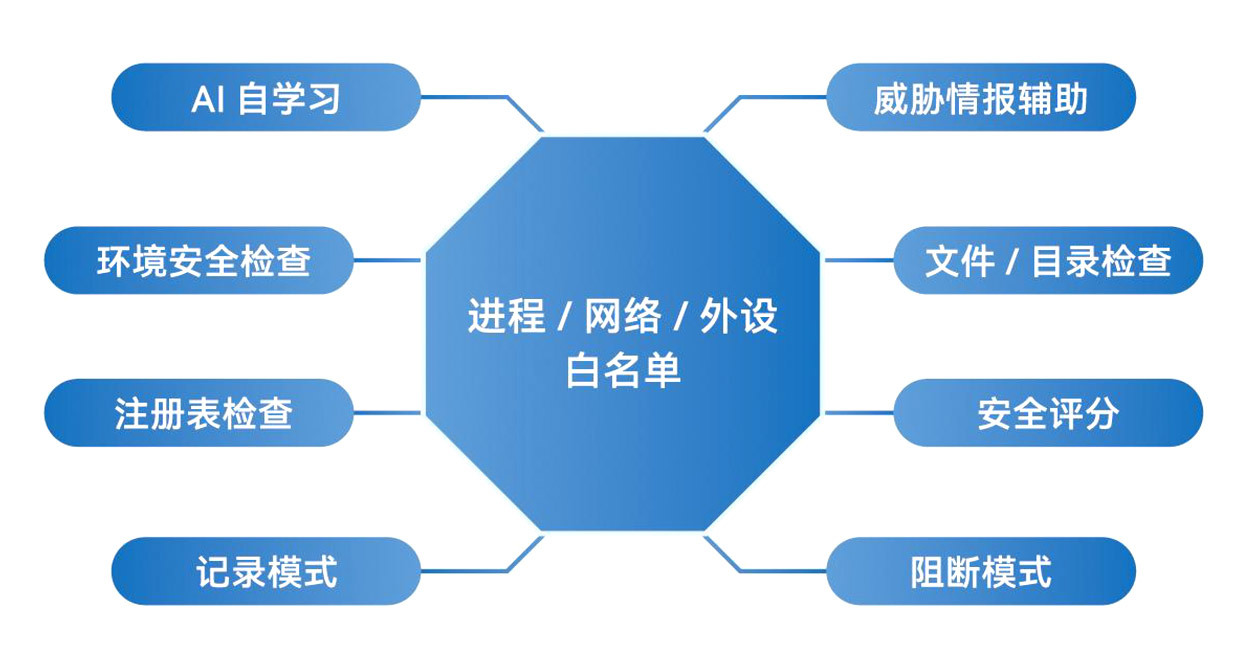
The product effectively ensures: Only secure and trustworthy files can be executed (supports standalone mode)
Only secure and trustworthy processes can run Only licensed processes can access licensed network links Only allowed external input devices are allowed to be connected and used Prohibit creating untrusted accounts or deleting trusted accounts Only terminals that meet the security baseline specifications are trusted Effectively resisting zero day attacks and advanced persistent threats (APT) Completely avoiding traditional antivirus software's "false killing" and "false alarms" Extremely lightweight and suitable for various old systems |
 |
Data Security Exchange System
| The data security exchange system mainly realizes various complex and heterogeneous massive data exchange business requirements such as file synchronization, database synchronization, and request response in cross network isolation environments, achieving seamless connection with business systems; It can also monitor the entire exchange process, achieving confidentiality, completeness, controllability, availability, and traceability of the entire exchange process. Suitable for users with cross network data exchange needs such as files, databases, requests and responses between different security domains in various industries. | |
|
High stability
The product itself supports load balancing and redundant hot standby.
Capable of handling exceptions such as network disconnection and reconnection, self start, and breakpoint continuation The exchange process is highly controllable
Support status monitoring and management for each exchange task.
Support real-time traffic monitoring. Support operational environment monitoring. Support the hardware resource usage and operating system load of the product itself. Support data exchange record auditing and statistical functions. Support alarm information prompts and comprehensive queries. High Compatibility
Support various file data exchanges.
Support isomorphic or heterogeneous data exchange between various databases. Support the exchange of various request commands and response data. Data exchange between domestic databases and big data databases. The mutual conversion of data between files and databases. The most widely used business application system adapter interface in the industry, seamlessly integrating various business system data. Seamless compatibility with major mainstream software and hardware platforms and development languages. |
 |
Industrial firewall system
| Industrial firewall system is an information security product designed and developed specifically for the network security of industrial control systems. Suitable for industrial control systems such as SCADA, DCS, PCS, PLC, etc., it can be widely applied to industrial control systems in areas closely related to national economy and people's livelihood, such as steel, chemical, petroleum and petrochemical, power, natural gas, advanced manufacturing, water conservancy hubs, railways, urban rail transit, urban water supply, gas supply and heating, and other fields. | |
|
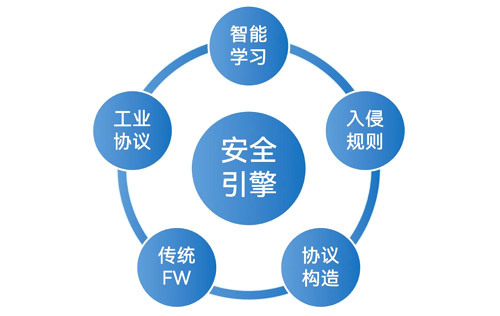
Basic functions: Equipped with basic firewall functions, including integrated access control based on traditional quintuples, protocols, assets, time, and other multiple groups; Support transparent, routing, and hybrid mode deployment; The device is equipped with multiple industrial protection models and can customize protection rules; Industrial DPI: supports deep parsing of various industrial protocols, including OPC, Modbus/TCP, Modbus/RTU, Ethernet/IP, IEC104, and EIP, and can achieve instruction level access control. Private protocol custom control: supports users to write filtering strategies for industrial data packets on their own, and can freely define bit level filtering security policies based on enterprise private protocols without the need for vendor participation, fully ensuring the security of private protocol definitions; Equipped with a scalable rule engine based on natural language descriptions, supporting custom message parsing, and possessing excellent security protection scalability. Online learning: Building a security protection architecture based on the technical roadmap of discovery, visualization, control, and assisted generation of strategies. Industrial VPN: Supports data encryption transmission based on industrial protocols. Centralized management: supports large-scale deployment of industrial firewalls, unified distribution of network policies, unified display of device conditions, and centralized display of log alarms. Log auditing: supports the recording and outsourcing of device management logs and system logs. |
 |
Copyright©2024 Bonin Fortune SEO Business License





